After collecting all the information you can about your target network its time to use this information for something dicey. If you place your router against an outside wall half of the signal goes out of your home.
Building A Test Lab For Pentesting Guide White Oak Security
And on a home network they are pretty likely to accomplish that goal.

. Penetration testing or pen testing is used to ensure that your enterprise is protected against cyberattacks and with a little work its possible to take care of the basics yourself. Place your router in a central location. When you first plug the device in and open the lid it creates a new WiFi network.
Get In Touch Today. Step 2 of this network penetration testing. Ensuring that your firewall is on and all the settings are properly configured will strengthen the network security of your network.
You can use tools such as Metasploit Nessus and PowerShell for this. The easiest thing you can do to secure your home internet connection is to change the default name. I Pick which exploit to use.
1 A computer with network monitoring tools installed I used a MacBook laptop 2 A network appliance with port mirroring capabilities in order to send a copy of all the. Placing the router in the center of the house will. Use routers that support the latest standard version of Wi-Fi currently Wi-Fi 6If your network includes more than one client connected through 5 GHz Wi-Fi use a tri-band Wi-Fi.
Lansweeper Can Scan Agentless or Agent-Based Depending On Your Needs. Make and storeusing either. How To Scope A Network Penetration Test Pentester Tips.
Proper reporting of results. Ad Enjoy low prices on earths biggest selection of books electronics home apparel more. Dont forget to disable the port.
Ad A Network Tool that Accurately Scans for Hardware Software Data from Connected Devices. If your stuff is decently patched current software and you dont use defaultbullshit credentials youre pretty. Regularly back up your data.
If you try to perform pen test on the public IP then ASA being a security device will block the attacks. Read customer reviews find best sellers. WiFi signals radiate in all directions.
Keep reading for more information on each below. Create a strong Wi-Fi. Easy enough to follow at home but because its a home merging workstation users and workstation admins is an obvious convenience I would recommend to anyone.
Get In Touch Today. Browse discover thousands of brands. Tips on how to secure your home network from.
Identify Threats to Your Organization Assets at Risk Threat Agents. The next is Wireshark a network protocol and packet analyzer that is important when it comes to penetration test tools. However should you want to pentest these areas you would need to obtain explicit permission from the end user to inventory.
Live data can be read from Ethernet IEEE 80211 PPP. These are just a few examples of the things you can do when pentesting your own network. Click on the Windows icon in the far left of your taskbar followed by Settings the cog symbol that appears just above it.
Once you connect to this network using your phone or computer you navigate to the router. Rarely are these part of a pentesting scope. Discovery After your organization has developed a strategy for the network pentest its time to initiate reconnaissance.
Proactively Defend Against Ransomware Exploitation Social Engineering Attacks. Ad Understand Real-World Risks Impacts of System-Vulnerabilities. No need to go.
Gain a Complete Understanding of Exploitable Vulnerabilities in Your Environment. Here are the basics for protecting your home Wi-Fi network. Penetration testing also known as pen testing is a simple term that means you are looking at your computer system to determine if it has any security vulnerabilities that.
Below we have explained how to ensure it is turned on. Change the default name and password of your home network. Ad Let Our Experts Conduct Internal External Pen Testing to Evaluate Your Vulnerabilities.
Ad Understand Real-World Risks Impacts of System-Vulnerabilities. If so this isnt necessarily a problem but it means that the previous test didnt test your router it tested the network connection to your router. Exploitation of the Wireless Network.
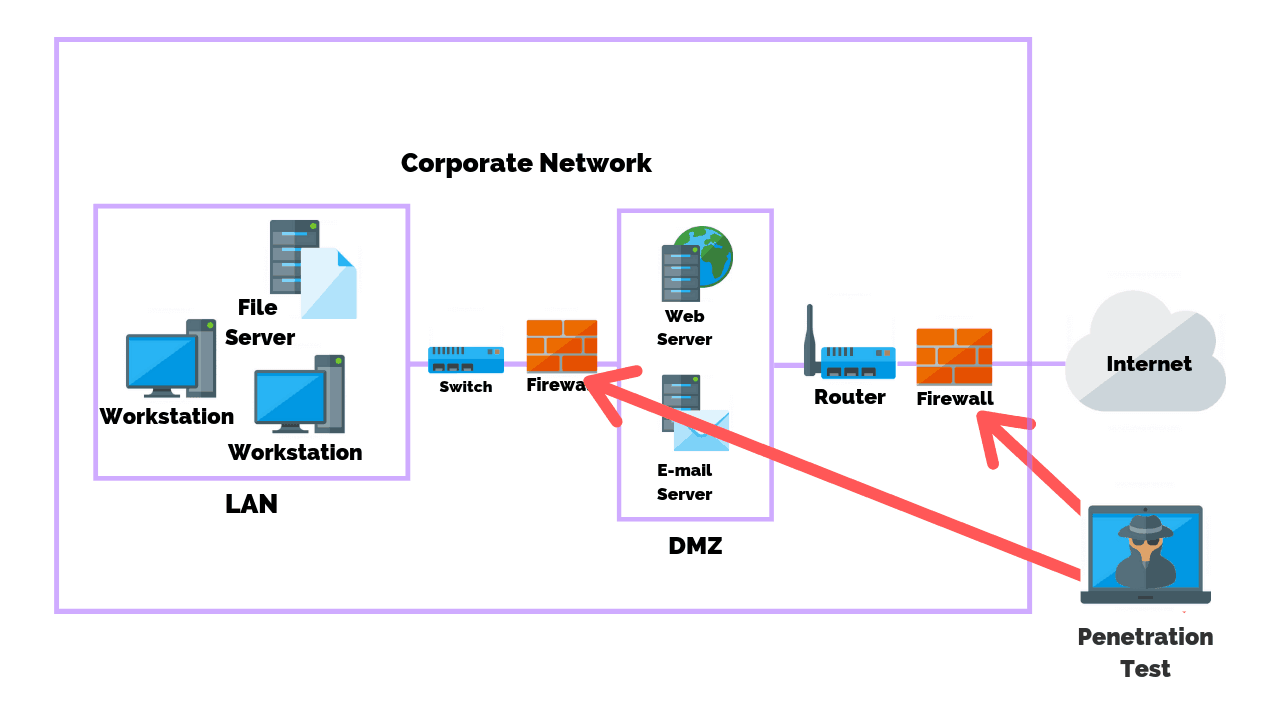
Firewall Penetration Testing Steps Methods Tools Purplesec
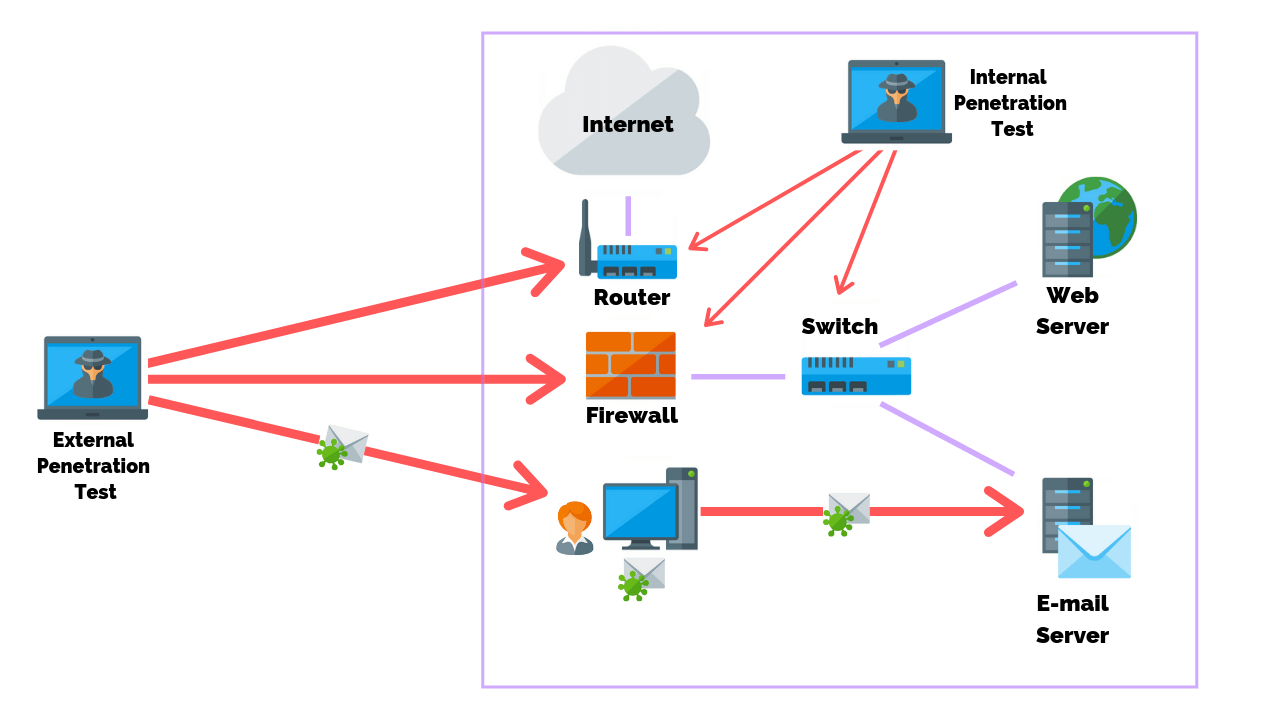
Firewall Penetration Testing Steps Methods Tools Purplesec
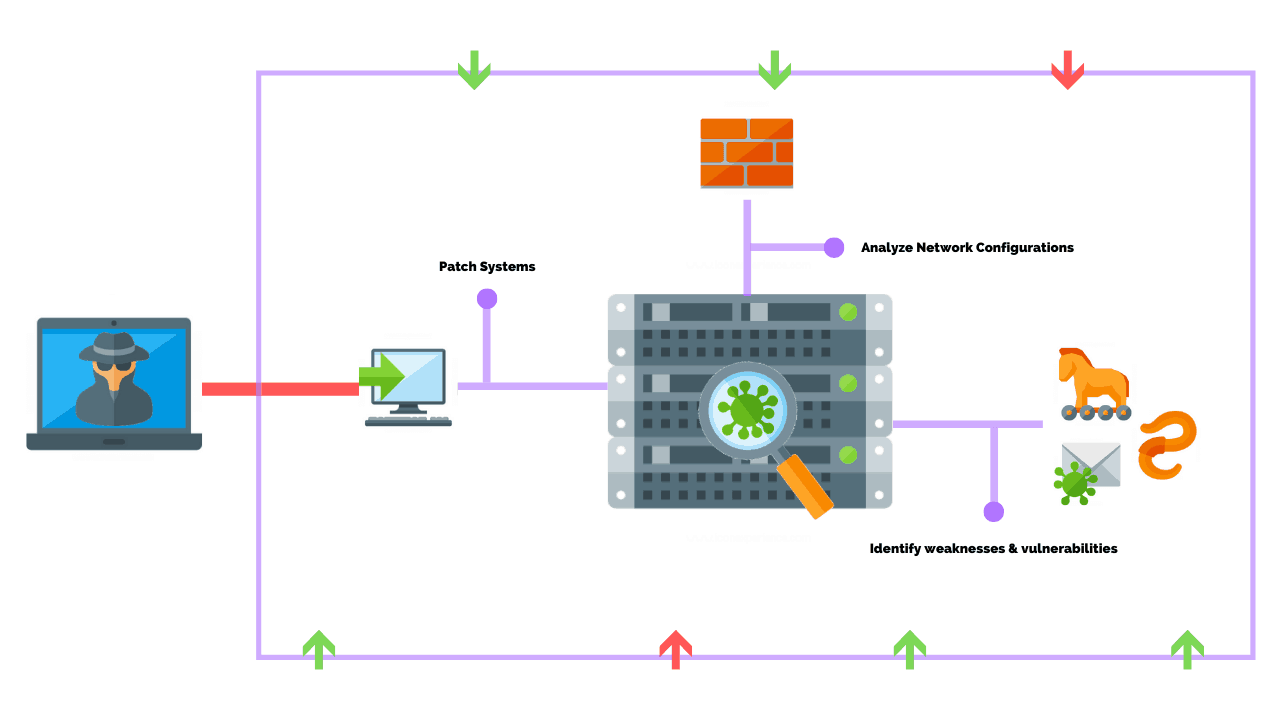
How To Perform A Successful Network Penetration Test Purplesec

How To Set Up A Pentesting Lab Rapid7 Blog
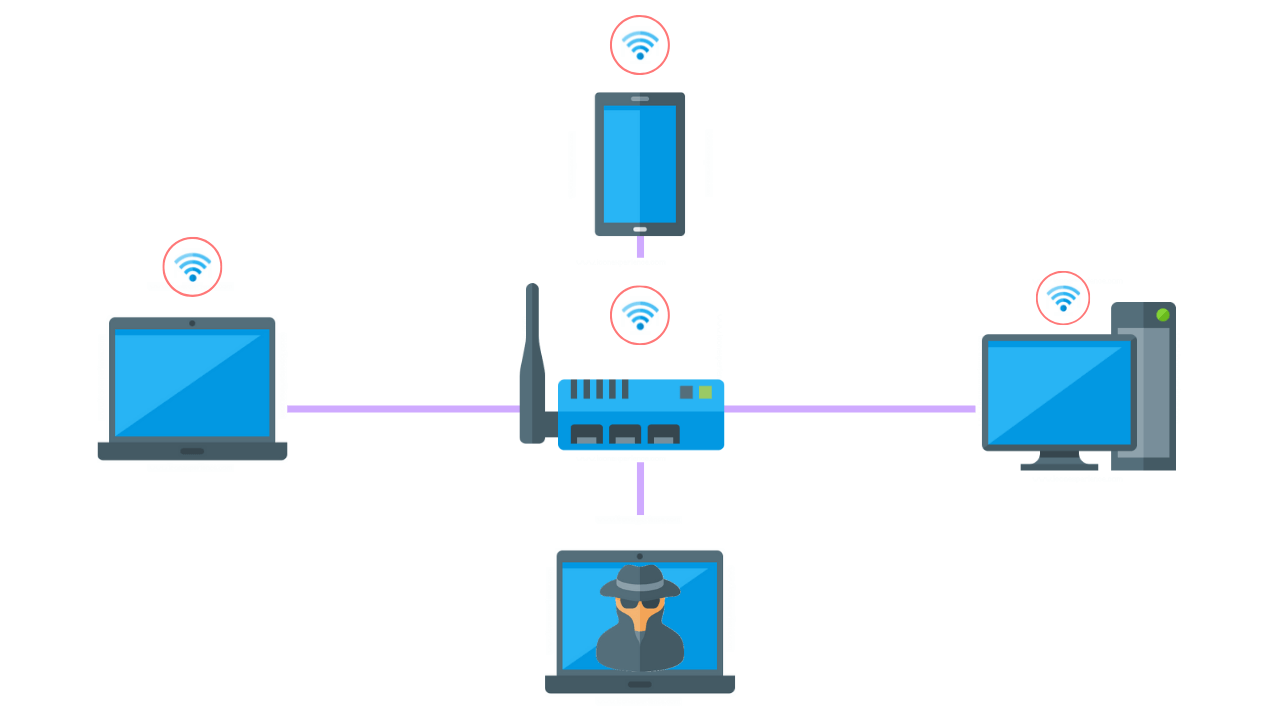
How To Perform A Successful Wifi Penetration Test

Hacking Your Home Pen Testing Your Local Network By Aliaksandra Havia Medium

Diy Penetration Testing To Keep Your Network Safe Pcmag

Ultimate Guide On How To Perform A Successful Network Penetration Test
0 comments
Post a Comment